The following sequence of Commands can be used in Windows native powershell to migrate an on-premise mailbox to O365.
$LiveCredential = Get-Credential
$Session = New-PSSession -ConfigurationName Microsoft.Exchange -ConnectionUri https://outlook.office365.com/powershell-liveid/ -Credential $LiveCredential -Authentication Basic -AllowRedirection
Import-PSSession $Session
$LocalCredential = Get-Credential
New-MoveRequest -id "test5@domain.com" -Remote -RemoteHostName "mail.domain.com" -TargetDeliveryDomain domain.mail.onmicrosoft.com -RemoteCredential $LocalCredential
It is worth noting that we should not launch these commands using Exchange Management Shell (EMS) as in that case we get the following error:
remote move request target user already has a primary mailbox
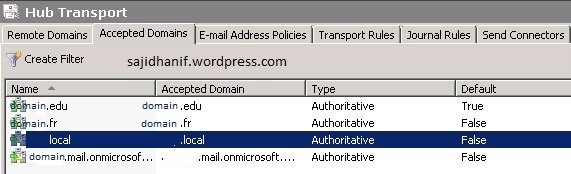
It is also imperative to know that if you have a different internal and external domain i.e. domain.local internally and lets say domain.com externally, it is recommended to remove domain.local from list of accepted domains.
The credentials for Office 365 need to be given in the format O365-admin@domain.com
The local credentials should be in the format domain\localAdministrator.
If you do not provide the local credentials you will get this error:
[outlook.office365.com] Connecting to remote server failed with the following error message: [ClientAccessServer=HE1PR02CA0029, BackEndServer=, RequestId=e655d769-b1a4-4a6c-b076-3ccd24909f58,TimeStamp=1/13/2016 1:51:26 PM] Access Denied For more information, see the about_Remote_Troubleshooting Help topic.